How can you protect your business from the very people who work with you?
While you might have everything in place to protect you from external cyber-attacks, unexpected security threats can come from right under your nose – even from good willed and trusted employees.
It’s all well and good to keep your data safe and secure, but it can just take one employee not following the right security protocols, or disgruntled ex-employees having access to data – and you might find your business in serious trouble.
With the majority of us working remotely, this brings with it a whole raft of security issues – do employees have access to the right servers for their work, are staff updating their apps and systems accordingly, are they using work laptops for personal use?
That’s why it’s so important to drill security practices into everyday actions for staff – while many basic security principles may seem obvious, the consequences of even a minor slipup can be severe.
So, how can you protect your business and data from well intentioned employees who might not be in the know about IT security?
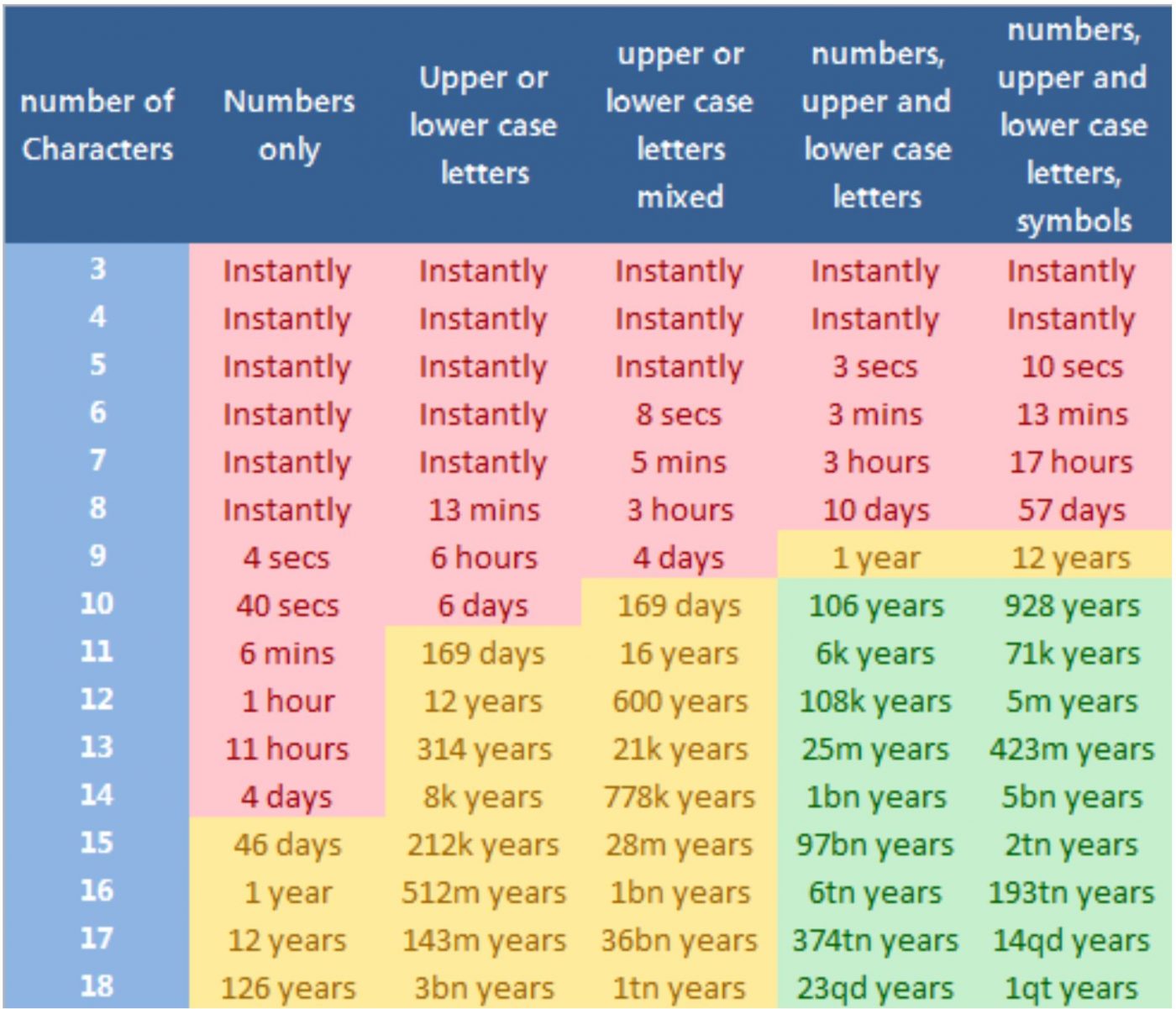
It starts with Cyber-Sensibility, ensuring your staff are well educated with regards to your company’s IT operations, passwords and keeping data confidential and secure.
Start by taking time out to train employees on IT best practices – saving documents to the correct files, ensuring passwords remain secure, and that employees know not to use their computers or laptops for personal use
Consider implementing a password manager for secure and confidential passwords and access to shared services)
Ensuring employees are well-enough educated in regards to cyber-security can be one of the most important methods to keeping safe.
A study conducted by Cyberark discovered over half of all employees are happy to allow co-workers using their login details, meanwhile 45% revealed they don’t tell IT when they download an unauthorised app to their device.
This sort of behaviour comes with severe risks of viruses and hacks, leaving IT systems much more vulnerable to attacks – it’s well worth double-checking staff understand basic IT security to protect themselves and the business.
The next step is to keep on top of remote setups.
The pandemic has seen unparalleled amounts of workers working remotely from home, which has completely moved the goalposts in terms of cyber-security.
A recent survey discovered 95% of security professionals were facing added IT challenges with employees WFH in thrown together home offices not fit for purpose.
Threats like phishing scams and malicious webpages are now having greater impacts than before, posing a huge threat to all businesses and employees.
Your IT security needs adapt to the changing environment, ensuring employees know what potential scams look like through training and flagging up anything they’re unsure about.
Be aware of what potential scams look like, through training and avoiding complacency, keep a distance from anything that could pose a threat, and ensure apps and systems are consistently updated.
What about ex-employees?
The process of removing moved-on workers from your system is another action that has to be taken seriously. It’s estimated that around 92% of UK businesses don’t automate this task as part of an off-boarding process, leaving plenty of room for human error.
Allowing a former employee to have access to your IT systems runs the risk of a whole load of IT security issues.
In fact, a Gurucul study discovered around one in ten workers would take as much corporate data as they could on the way out of a job, with a further 15% saying they would change passwords and even delete files.
Of course, not everyone will take files or change passwords, but that doesn’t mean you shouldn’t be meticulous about your offboarding processes and take all the necessary precautions to prevent data breaches from former employees.
Much of the time, departing staff might not have any ill will but can still leave your business open to data breaches by keeping business files and information on personal computers, failing to handover correct log in details, and not returning all of their company IT equipment.
There are a few ways you can look to prevent this such as wiping work-devices, changing passwords, and removing access to files (especially company social media accounts) and notifying the IT department well in advance about staff changes.
How can we help?
Getting the best IT advice is essential to help prevent breaches and security issues from damaging both your reputation, your business, and your profits.
If you’re interested in how you can improve your business security, please get in touch with our friendly team of IT experts – who will run through everything cyber-related with you.
You can find out about all of our different services here