Microsoft is rolling out a significant security upgrade: the new ‘Number Matching’ authentication process.
You are probably thinking you’re just getting the hang of 2 Factor Authentication and now the process is changing – again!
Never fear CIT promises to make it simple to understand and easy to implement. First of all, let’s tell you a bit about Number Matching and why it matters.
About Number Matching
Number matching is almost the opposite of what you know as multi-factor authentication. With this new authentification process, a user will see a number when they sign in. The user will then confirm this number on their MFA device.
Don’t worry, there is help for end users who cannot meet sign-in criteria with a ‘Temporary Access Pass’ feature.
Why is number matching coming?
The number one reason is to stay one step ahead of cyber criminals. Sophisticated cyber criminals have devised techniques to bypass Multifactor Authentication, register and authenticate their own device enabling them to override approvals.
Do I need to do anything?
As long as you have the Microsoft Authenticator installed on your device, you shouldn’t need to make any changes.
How do I check Microsoft Authenticator is installed?
You can check Microsoft Authenticator (traditional second factor) is turned on for some users or groups. You can do this by editing the Authentication methods policy. If your organization uses AD FS adapter or NPS extensions. Make sure you have the latest versions before you start.
How do I enable number matching in the Azure AD portal?
Here is Microsoft’s steps to take in the Azure AD portal. Complete steps:
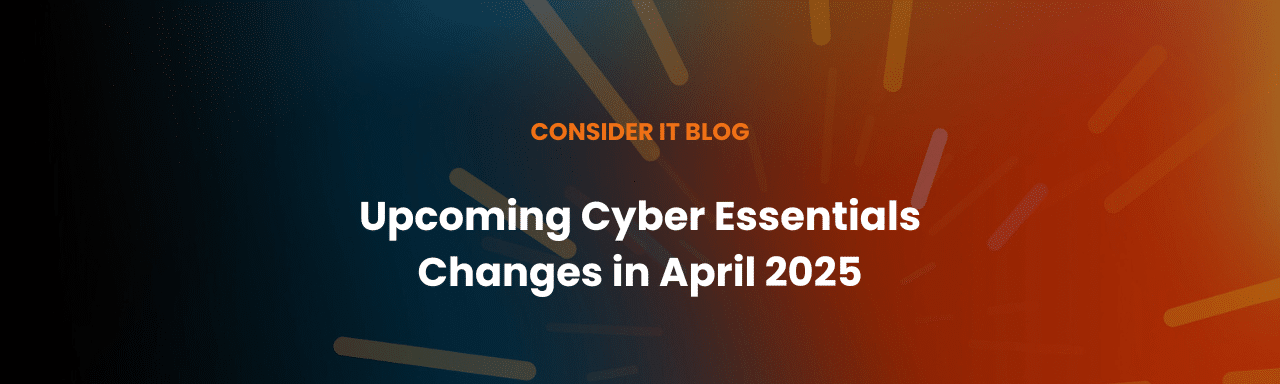
- In the Azure AD portal, click Security > Authentication methods > Microsoft Authenticator.
- On the Enable and Target tab, click Yes and All users to enable the policy for everyone or add selected users and groups. Set the Authentication mode for these users/groups to Any or Push.
Note: Only users who can use Microsoft Authenticator can be a part of this policy or not be a part of it. Users who cannot use Microsoft Authenticator cannot see this feature.
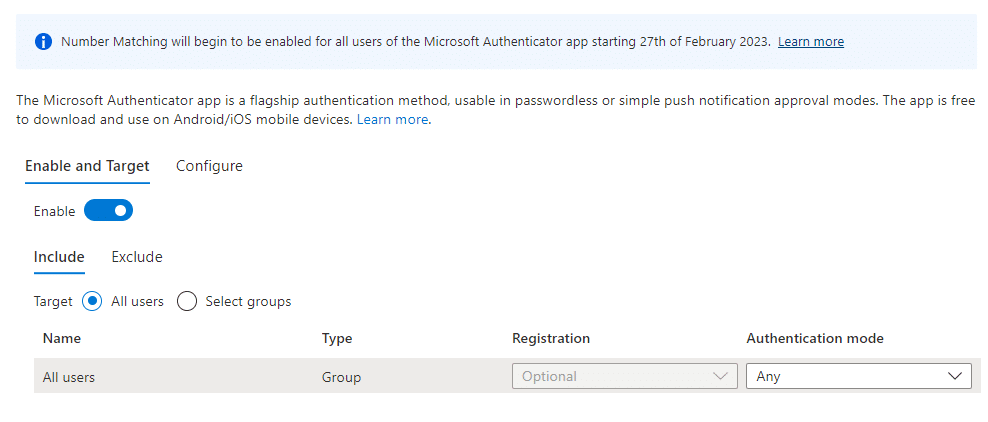
- On the Configure tab, for Require number matching for push notifications, change Status to Enabled, choose who to include or exclude from number matching, and click Save.
You can read full Microsoft instructions on how to MFA number match at ‘How to MFA number match.
When is Number Matching available?
- When someone is trying to log in with more than one factor
- When someone is resetting their password themselves
- When someone is registering for an Authenticator app and they’re using more than one factor
- When someone is using AD FS adapter (Active Directory Federation Services is a Single Sign-On solution)
- When someone is using NPS extension (Network Policy Server extension for Azure Multi-Factor-Authentication
A final note for Apple Watch Users.
It’s important to be aware Number Matching isn’t available when people are getting Apple Watch notifications. If number matching is turned on, people will need to use their phone to approve notifications from their Apple Watch.
In case you missed it here is the link again for detailed ‘How to MFA number match‘
Get in touch for expert IT Support
Find out more about our Managed IT services so you can focus on managing everything else in your business.